In the end it's all about Heisenberg's uncertainty principle and the no-cloning theorem. Heisenberg's uncertainty principle tells us that at the quantum level certain physical properties of an object cannot be defined simultaneously and that translates into a fundamental uncertainty - quantum noise - on how well we can measure those properties at the same time. Physical properties showing this kind of uncertainty are known as non-commuting observables. For light, examples are the polarisation observables of a single photon (this is the degree of freedom used in BB84) and the amplitude and phase of a continuous laser beam (that's the relevant one for CV-QKD).
Classical optical communication
Before we go deeper into it, let's take a brief detour to classical optical communication. The world is interconnected with optical fibres that allow us to transmit digital information over long distances and with high speed using laser light as the carrier medium. A characteristic of laser light is that it is single frequency and we can think of it as a wave oscillating with stable frequency and phase. This type of optical state is also known as a coherent state. By applying modulations to the light wave that wiggles its amplitude (AM) and phase (PM) we can create new coherent states with precisely controlled amplitude and phase by tuning the respective modulation strengths. In this way we can build up an alphabet of optical states and use them to encode information. This is what's done in e.g. Quadrature Phase-Shift Keying (QPSK).
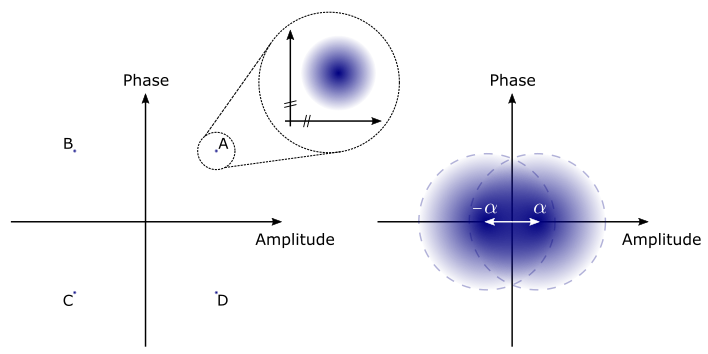
Classical optical communication uses optical modulation to generate an alphabet of distinguishable optical states for encoding of information (left). When the modulation is weak, quantum noise makes the states overlap and hence partly indistinguishable (right). This is exploited for CV-QKD.
Useful noise
Now, if we zoom in on the alphabet states we notice that they are in fact not dots but blurred blobs. This "blur" is quantum noise, and it is a result of Heisenberg's uncertainty relation between the amplitude and phase quadratures. In optical telecommunication we don't care about this noise. We just modulate strongly enough that the alphabet states are effectively point-like and can be perfectly discriminated.
For QKD, we do exactly the opposite. Using only weak modulations, we create states that are not indistinguishable because their quantum noise overlaps. In the simplest case, we generate just two different states with a slight separation, as illustrated above - the one state representing a binary "0" and the other a "1".
A QKD setup consists of a transmitter and a receiver. The transmitter generates a long stream of quantum states, in each case randomly picking a "0" or "1" encoding, and transmits that to the receiver. On the receiver side, a random choice is made on what property to measure for each of the exchanged states and the results are logged. In the event that the receiver measurement is compatible with the transmitters encoding, the encoded bit value is faithfully recovered. In the opposite case, the receiver generates a random bit. Following the exchange of quantum states, transmitter and receiver communicate via an authenticated classical channels, exchanging information about how the states were encoded and measured. The bit strings on either side are then decimated, keeping only those corresponding to compatible encoding and measurement choices.
The fact that the transmitted states cannot be discriminated means that a hacker also cannot tap into the transmission line and figure out the encryption key that the two parties are going to use when they start transferring data. And if he does try, he will always leave a noticeable trace. Consider the simplest type of attack the hacker can do: intercept and resend. In this case he does just like the receiver - he measures the states sent by the transmitter randomly, records the results, and then prepares states identical to what he has measured and resend them to the receiver. However, the states from the receiver are effective superpositions of "0" and "1" and each measurement will yield random results. With a certain probability he will get the same result as recorded by the transmitter and with another probability the opposite. When the hacker intercepts and resends he breaks the original probability distribution for transmitter and receiver to obtain identical/opposite results and that change can be detected. And that is exactly what the transmitter and receiver stations will do in the post-processing step. As soon as a discrepancy is flagged the key exchange is aborted and restarted.